NIST CSF Introduction
Version 1.0 of the National Institute of Standards and Technology Cybersecurity Framework was issued in February 2014 and provides a framework for improving critical infrastructure cybersecurity. Version 1.1 released in April 2018 refines, clarifies, and enhances version 1.0 of the NIST Cybersecurity Framework (CSF).
The National Institute of Standards and Technology is currently working on version 2.0 of the NIST CSF.
Find the latest version of the NIST CSF at: NIST CSF
This article as an overview of the NIST Cybersecurity framework and is not meant to drill down to deep. Separate articles drill down on each function in greater detail.
Table of Contents
Organizational Benefits from NIST CSF
Based on security practices known to be effective, the NIST Cybersecurity Framework (CSF), establishes a set of standard security functions and outcomes. Organizations can use the NIST CSF to improve their cybersecurity posture. It helps organizations foster communication about cybersecurity internally and externally and allows organizations to integrate and align cybersecurity risk management with enterprise risk management processes.
Introduction to the five (5) NIST CSF Functions
The NIST Cybersecurity framework is organized on 5 key functions:
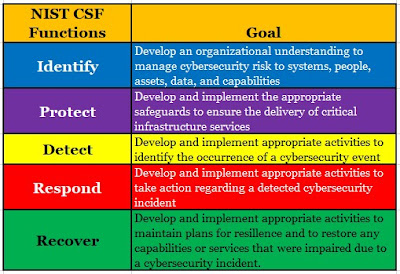 |
| NIST CSF Function Table |
These five (5) functions are a comprehensive view of managing cybersecurity risk over time. Each function is an important aspect of cybersecurity and all functions are needed to have an effective cybersecurity posture.
NIST CSF Identify
The NIST CSF Identify function helps to develops the ability to manage cybersecurity risk to: systems, assets, data, and capabilities. It involves inventorying assets, systems, and data to determine what needs protecting.
The NIST CSF Identify function helps to:
- Identify critical enterprise processes and assets
- Document information flows
- Maintain hardware and software inventory
- Establish policies for cybersecurity that include roles and responsibilities
- Identify threats, vulnerabilities, and risk to Assets
NIST CSF Protect
The NIST CSF Protect function is focused on putting in place the appropriate safeguards to ensure delivery of services. So, implementing the protection mechanisms to ensure critical information systems and operational systems are protected and in service.
The Protect function helps to:
- Manage access to assets and Information
- Protect Sensitive data
- Conduct regular backups
- Protect devices
- Manage device vulnerabilities
- Train Users
NIST CSF Detect
- The Detect function helps to:
- Test and update detection processes
- Know the expected data flows for your enterprise
- Maintain and monitor logs
- Understand the impact of cybersecurity events
NIST CSF Respond
The NIST CSF Respond function ensures the appropriate activities and mechanisms are in place to take appropriate actions when a cybersecurity event is detected. The Respond function is all about taking swift action when a cybersecurity event happens to contain and prevent any further impacts.
The NIST CSF Respond function helps to:
- Ensure response plans are tested
- Ensure response plans are updated
- Internal and external stakeholder coordination is managed and in place
NIST CSF Recover
The NIST CSF Recover function ensures appropriate activities are in place to maintain plans for resilience and to restore systems, capabilities, or services impaired due to a cybersecurity event. The respond function is focused on recovery or restoring any services that were impacted due to a cybersecurity event.
The NIST CSF Recover function helps to:
- Communicate with internal and external stakeholders
- Ensure recovery plans are updated
- Manage public relations and company reputation
NIST CSF Implementation Tiers
NIST defines Implementation tiers for the Cybersecurity framework. The Tiers denote increasing degrees of rigor and maturity regarding cybersecurity risk management practices. The tier levels help with determining the extent to which cybersecurity risk management is informed by business needs and is integrated into an organization’s overall risk management practices.
Tiers are defined to support organizational decision making on how to manage cybersecurity risk, as well as helping to determine the dimensions that are higher priority for an organization and should receive additional resources. Obtaining higher tiers is encouraged when it is determined to be feasible and cost-effective for reduction of cybersecurity risk.
The Tier definitions are as follows:
- Tier 1: Partial
- Tier 2: Risk Informed
- Tier 3: Repeatable
- Tier 4: Adaptive
Conclusion
The NIST Cybersecurity Framework is important for increasing an organizations security posture. The NIST CSF is built based on security practices that are known to be effective. This is extremely helpful to organization in improving cybersecurity risk management practices. NIST CSF is organized around 5 functions, Identify, Protect, Detect, Respond, and Recover. The NIST Cybersecurity framework also helps to foster communication across internal and external stakeholders allowing organizations to work more collaboratively to improve the cybersecurity posture across the enterprise.
Finally NIST CSF establishes four (4) implementation tiers and are defined to help with organizational decision making on how to manage cybersecurity risk. The four implementation tiers are: Tier 1: Partial, Tier 2: Risk Informed, Tier 3: Repeatable, Tier 4: Adaptive




